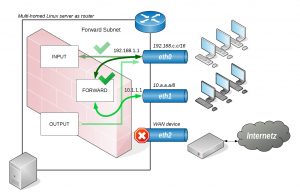
FORWARD_SUBNET
Once some subnets are able to talk to the router things get interesting especially when to decide which subnet is allowed to reach each other or allowed to access services on the router.
Let’s say we have another private class A subnet (10.0.0.0/8) connected to the router. Hosts from that subnet on eth1 should be able to connect to hosts on the subnet (192.168.0.0/16) on eth0 interface without access to services running on the router itself !
Since the router wouldn’t talk to anyone it explicitly knows, we need to configure an IP address (10.1.1.1) on the eth1 interface to have a route from the subnet to be physically reachable but without allowing the subnet in the firewall. This time we won’t use a makefile but allow forwarding temporarily eg:
me@host:~# ipturntables.sh -4 FORWARD_SUBNET 10.0.0.0/8 eth0 # forwarding 10.0.0.0/8 (eth1) to eth0.
The FORWARD_SUBNET call doesn’t take any protection measures and is therefore recommended only for forwarding internal subnets on different interfaces where protection isn’t needed. We also omit service discovery, UPNP or link-local traffic. When only FORWARD_SUBNET call is given it would just allow hosts from the class A subnet on eth1 to pass the interface barrier by forwarding to the eth0 interface but without having access to service discovery, UPNP or link-local since this traffic still can’t pass when going through different interfaces and would need an explicit ALLOW_SUBNET on the router’s interface.
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- eth0 eth1 0.0.0.0/0 10.0.0.0/8 state NEW /* FORWARD_SUBNET 10.1.1.0/24 on 0x000e0c35edae to eth0 */
0 0 ACCEPT all -- eth0 eth1 0.0.0.0/0 10.0.0.0/8 state RELATED,ESTABLISHED /* FORWARD_SUBNET 10.1.1.0/24 on 0x000e0c35edae to eth0 */
0 0 ACCEPT all -- eth1 eth0 10.0.0.0/8 0.0.0.0/0 /* FORWARD_SUBNET 10.1.1.0/24 on 0x000e0c35edae to eth0 */
2555 319K LOG all -- * * 0.0.0.0/0 0.0.0.0/0 limit: avg 8/min burst 16 LOG flags 0 level 4 prefix "[FW4-DROP] "
Even when there would be other subnets (eg. 10.10.10.0/8) configured on eth1 they would end up denied because FORWARD_SUBNET explicitly accepts only traffic from the specified subnet and only between the given interfaces they reside on although traffic originating from the class A subnet can be addressed anywhere it’s limited to subnets on the eth0 interface only which is in our case the class C subnet.